Introduction
DHCP short for Dynamic Host Configuration Protocol) is one of the most important service to have is a network. This protocol serves the advantage of providing clients information such as IP address, subnet mask, DNS server, default gateway dynamically rather than configuring each host statically. This server start a process called (DORA) short for Discover, Offer, Request, Acknowledge. The process starts with the server listing on port 67 for discover requests on the network sent by clients. When a client sends out a discover packet across the network the server sees it and respond back with an offer providing the “offered” IP address over to the clients who is listening on port 68. The client then requests that IP address from the server and the server confirms that request by sending an ACK packet back.
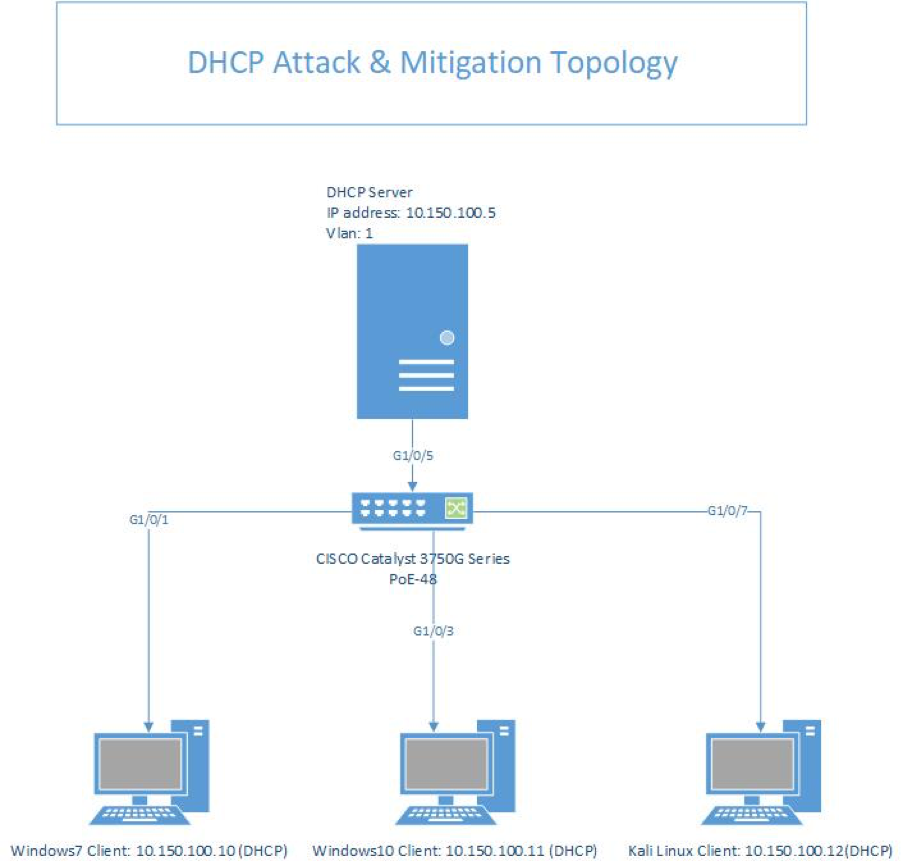
Topology
DHCP Attacks
DHCP Starvation
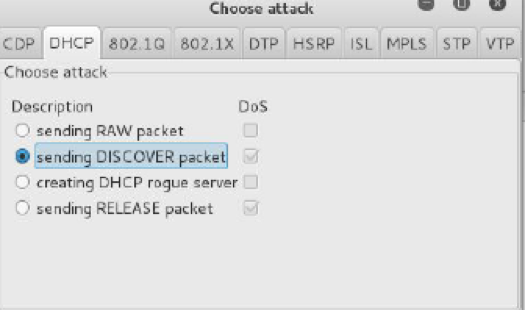
DHCP Starvation is an attack wherein the attacker looks at the entire DHCP scope and tries to acquire all the available address in that scope. This attack is considered a Denial of Service attack, as other clients will not be able too receive IP addresses anymore. Over time, the adversary continues to use new MAC addresses to send renewals for all the DHCP leases. In order to perform this kind of attack we can use a tool called yersinia. This tool is powerful as it provides plenty of low level networking attacks. By opening up the tool using this command yersinia -G and click on DHCP attack as show below, we can undertake the attack. Moreover, we can see the Wireshark traffic Which shows a heavy amount of Discover packets.
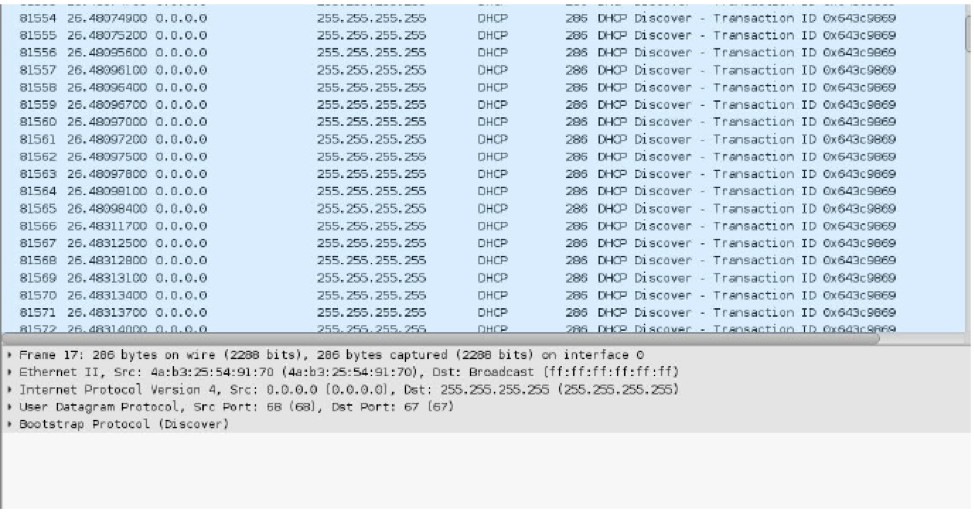
Here is a wireshark snippet during the DHCP starvation attack
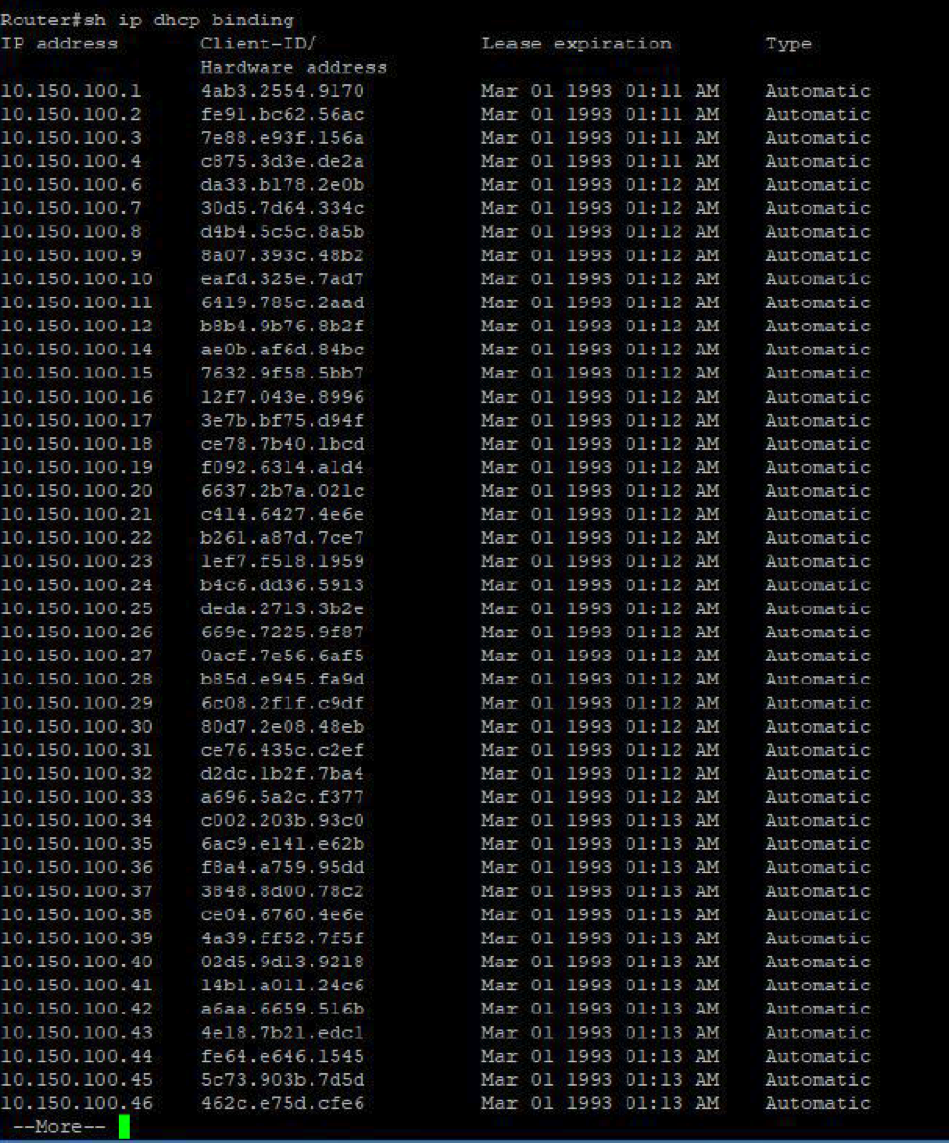
Now if take a look at the switch configuration by typing the command show ip dhcp binding we can see the all the addresses in scope have been acquired by fake/forged MAC addresses generated by Yersinia
DHCP Spoofing / DHCP rogue server
A DHCP rogue server attack occurs when an attacker acts as a legitimate DHCP server in which he gives out DHCP information., including: IP addresses, gateways, and DNS. To performt his attack the “ettercap” tool can be used. To start this tool use the command ettercap -G and click on DHCP attack. Moreover, we can see Wireshark traffic which show heavy amount of Discover packets.
Here is a wireshark snippet during the DHCP rouge server attack
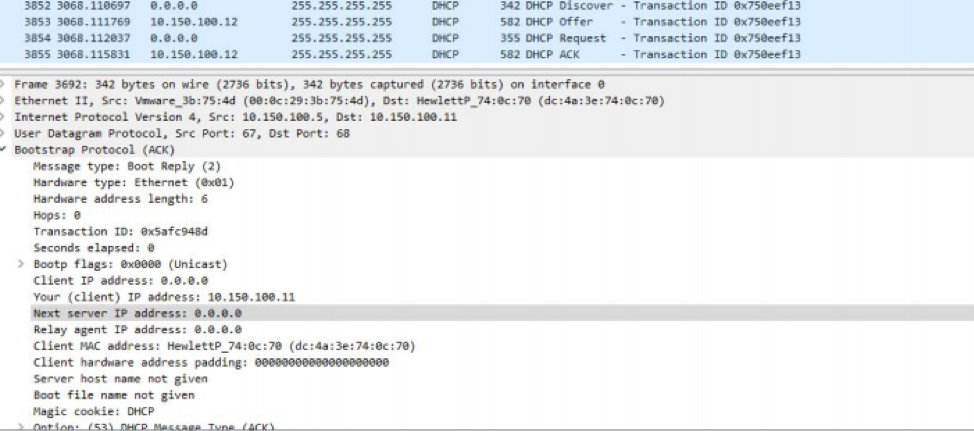
It’s worth noting that the address of our spoofed DHCP server is 10.150.100.12.
DHCP Attacks Mitigation
Moving on to how to prevent this attack, we can say that Cisco already has a security feature that is capable of identifying trusted and untrusted host. This feature is called DHCP snooping which has the ability to validate messages from untrusted host and drop them. In addition, it can evaluate DHCP traffic from trusted and untrusted host. This feature requires an offer binding database which has information about trusted and untrusted hosts. In our example, we can see that the port FE0/5 is trusted which means the DHCP server resides on that server.
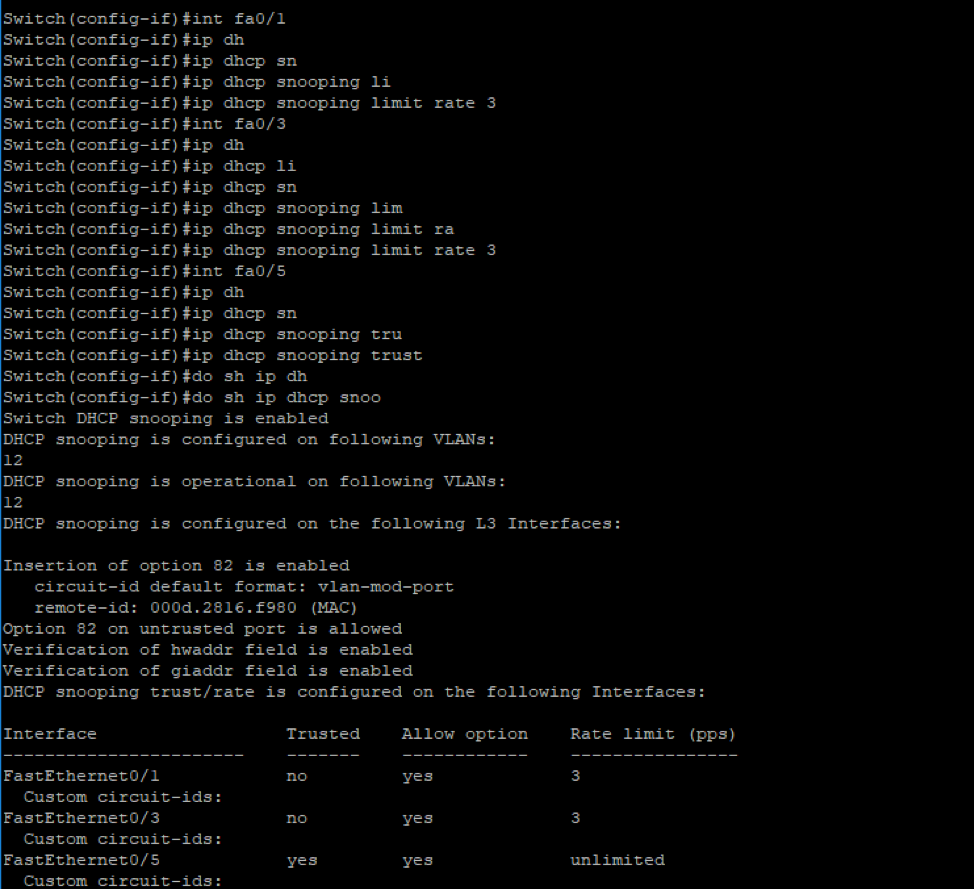
Switch Configuration for DHCP Snooping Now if we look at the Wireshark capture when the attacker tries to send an OFFER packet back to the victim. We will see the packet gets ignored by the victim and only respond back to the legitimate DHCP server
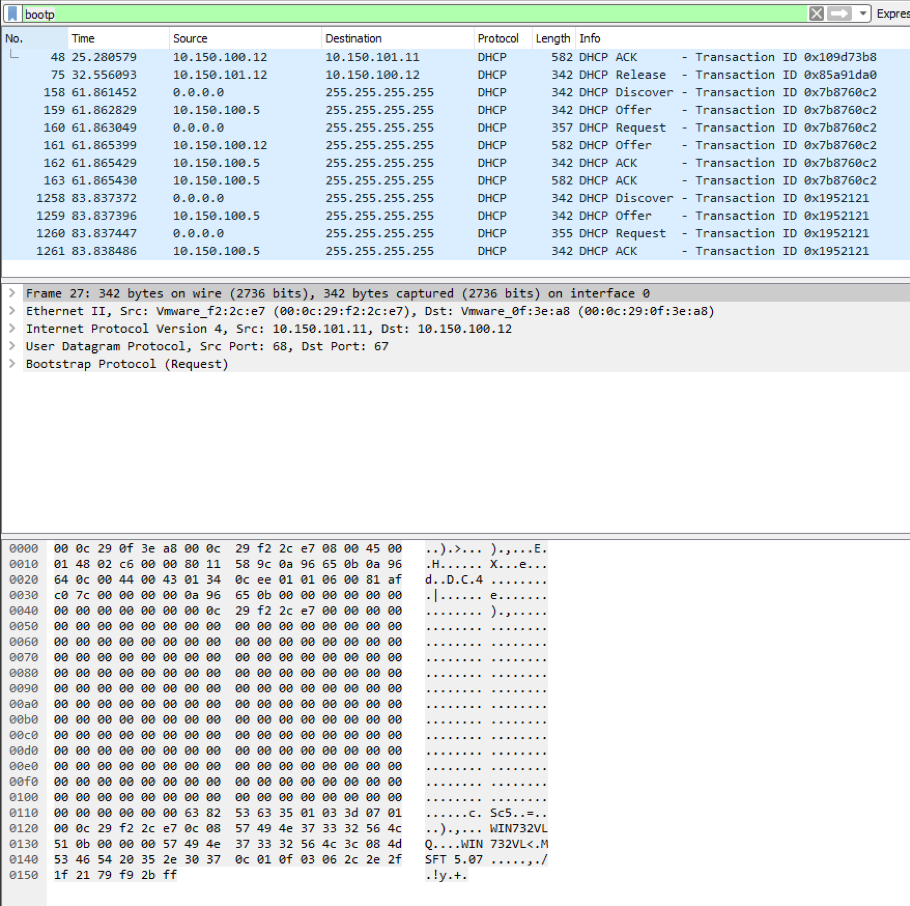
Wireshark Capture after DHCP Snooping is Configured So, only the packet that is formed by the legitimate DHCP server on the trust port is the only packets that gets advertise to the DHCP client and start the DORA process.
Conclusoin
From this experiment in DHCP Snooping Attack, it’s obvious that this attack leads to compromising the hall connection between two ends which is known as “Man in Middle Attack”. And “DHCP Snooping” and “trusted ports” features in Cisco switches have the ability to prevent illegitimate servers to acting as DHCP server. Thus, DHCP Snooping is acting as a firewall for preventing this attack.